OSINT Cybercrime Investigations
Investigate anonymous threat actors by identifying and attributing anonymous risks targeting your organization with Hunter OSINT Investigations.
REQUEST A DEMORead how leading cyber investigative journalist Brian Krebs used Constella Hunter to fight against cybercrime:
Constella’s Role in Fighting Cybercrime: Supporting Investigative Journalism and Law Enforcement
Today’s cybercriminals are more advanced and better funded than ever before. They operate with a high level of anonymity, using underground forums, aliases, and cryptocurrency to obfuscate their activities and hide their identities.
This makes your job of disrupting these adversaries increasingly difficult, requiring innovative data scouring and collection methods to uncover critical intelligence that will move an investigation forward.
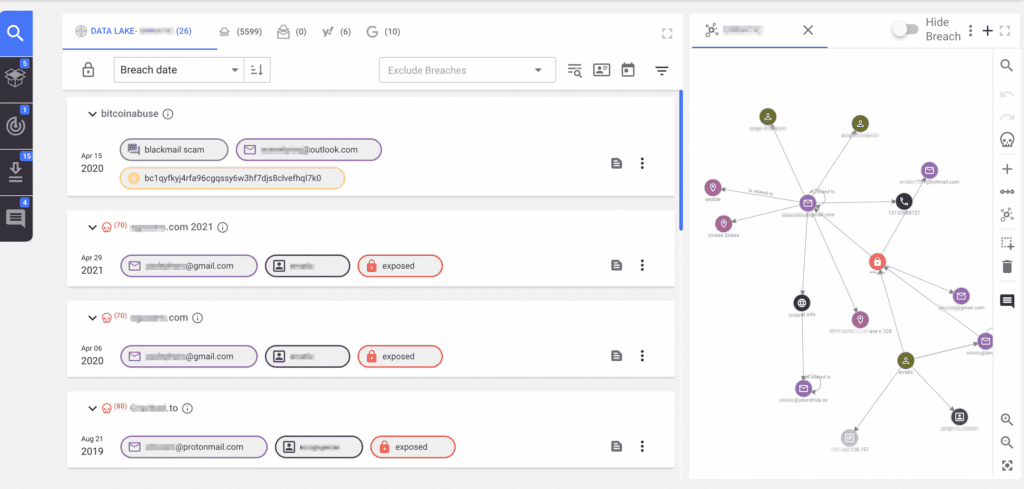
Constella Hunter is an intuitive cyber investigation tool that enables you to rapidly attribute malicious activity, fraud, and potential insider threats. With Hunter, you can analyze data from thousands of sources, collate and compare it across sources, and identify unknown connections and networks of activity.
Solve Investigations 5X Faster
Hunter delivers real-time and historical identity intelligence that helps you solve cases 5X faster. Hunter discovers the hidden connections that other tools and teams miss with its unique analytics engine and massive scalability. Hunter is designed to accelerate and simplify investigations and threat analysis by:
- Bringing together data from thousands of sources.
- Providing full customization of the queries to deliver high-value results.
- Enabling visualization of intelligence in an easily consumed format.
Unmatched Visibility
Hunter collects data from across the Surface, Deep, and Dark Web, and social media. It combines data from these thousands of sources with the Constella Data Lake™, containing over 124 billion compromised identity records, delivering unmatched visibility of threat actor activity.
Hunter Highlights
-
Single Indicator is All You Need
Start with a single indicator and enrich information from other sources and begin making connections, in real-time.
-
Correlated Data
Correlate activity across data sources to identify new accounts and data associated with your target.
-
Data Visualization
Build data visualizations in a graphical format that enables you to understand links and conduct advanced analysis.
-
Integrated Automation
Create profiles automatically based on commonalities of results using the AI-based classifier.
Fast, Simple Searches
Focus your search using a simple and intuitive search bar. You can search for over 30 different attributes and keywords across multiple sources (either individually or one at a time).

-
Link data from Surface, Deep, and Dark Web and Social Media sources and easily move between them.
-
Search the Constella Data Lake™ to access 124+ billion compromised identity records.
-
Conduct a bulk search, identify related searches, view your search history and investigate domain exposure.
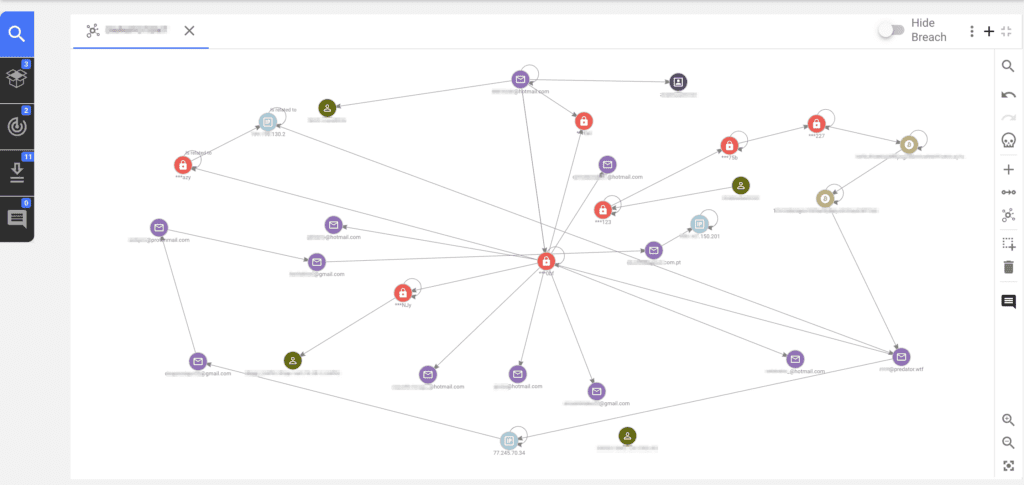
Visualizations
Why Customers Choose Hunter
-
Unique, Rich Data Sources
Discover hidden connections and tools that fuel criminal activity.
-
Attribution, Pivot & Enrich Data
Break down traditional barriers across data silos; Link real identity information to obfuscated identities & malicious activity: solve investigations 5x faster.
-
Relationship Graphing & Investigation Management
Build and collect evidence and submit to LEA / Dept of Treasury; decrease losses and reduce risk of future attacks.
-
Seasoned Team with a Single Mission
The Constella team consists of intelligence community analysts, infosec pioneers, military veterans and tech entrepreneurs with a single mission: Empower organizations to know their adversary and disrupt malicious activity.
See Constella in Action
Constella.ai is the global leader in AI-driven identity risk and deep and dark web intelligence for such applications as identity theft, insider risk, synthetic identity fraud detection (Advanced KYE/KYB), and deep OSINT investigations.
With the world’s largest breach database, containing over one trillion data attributes in 125+ countries and over 53 languages, Constella empowers leading organizations across the globe to monitor and secure critical data through unparalleled visibility and actionable insights.
Digital Risk Protection Platforms
Executive and Brand Digital Protection
Subscribe To The Constella Newsletter
©2025 Constella Intelligence. All rights reserved. Website Privacy Policy. Terms of Use. Datalake Privacy Notice. Acceptable Use Policy.

